Today where your toaster, thermostat, fridge, car, and even your pet feeder are all connected to the Internet, there’s no denying that the Internet of Things (IoT) is here to stay and it’s only growing bigger by the day.
But as cool as it is to tell Alexa to start your coffee machine or let your smart lock open with your phone, there’s a dark side to all this connectivity. And that dark side is IoT security or rather, the lack of it.
Let’s break down what’s happening, why it matters, and what you can do to stay protected in this new digital wildwest.
What is IoT?
IoT refers to the network of physical objects (“things”) that are embedded with sensors, software, and connectivity. These devices collect and exchange data with other systems and devices over the internet.
Examples include:
- Smart home devices (bulbs, locks, thermostats)
- Wearables (smartwatches, fitness trackers)
- Industrial sensors (for machines, pipelines, temperature, etc.)
- Connected vehicles
- Medical devices (heart monitors, insulin pumps)
- Smart agriculture tools (soil sensors, irrigation systems)
Essentially, if it has an IP address and collects data, it’s part of the IoT ecosystem.
The Rise of IoT (and Its Security Problem)
According to Statista, there will be over 30 billion connected IoT devices by 2030. That’s roughly 4 devices per person on the planet.
But here’s the catch: most of these devices were never designed with security in mind.
In the rush to innovate and hit the market, many manufacturers cut corners on cybersecurity. Some devices ship with hardcoded passwords, others never receive software updates, and many use outdated protocols that are easy to exploit.
It’s like building a futuristic smart city but forgetting to put locks on the doors.
Why IoT Devices Are Easy Targets
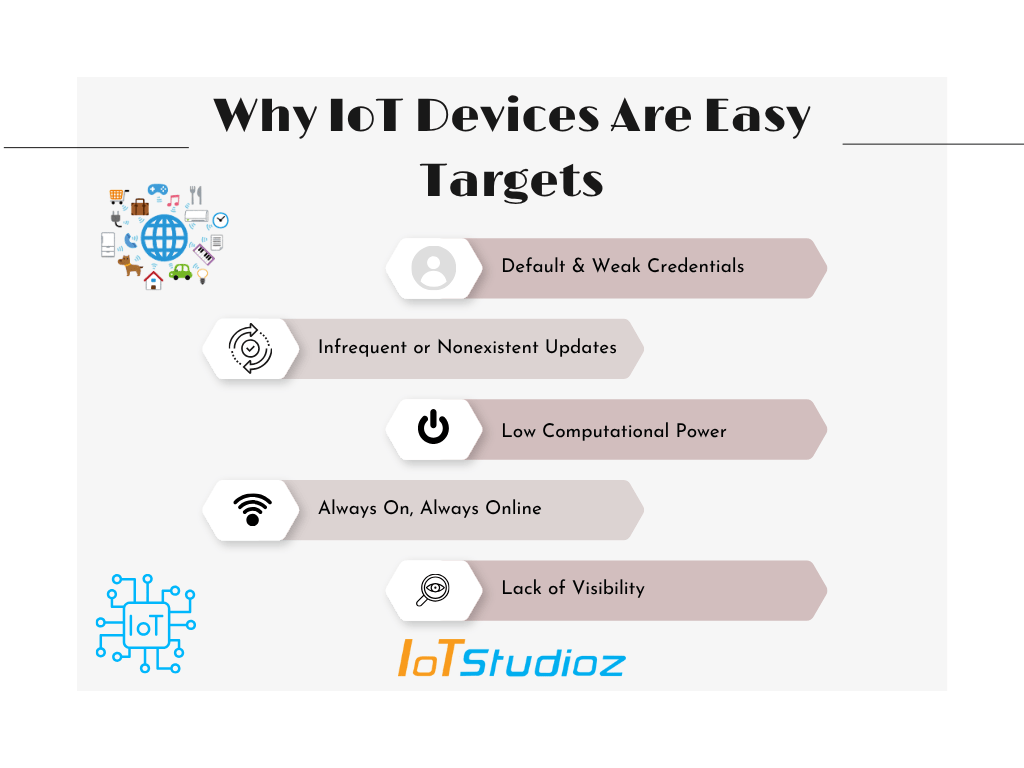
1. Default & Weak Credentials
Many IoT devices come with default usernames and passwords like admin/admin or 123456. Worse? Users often don’t bother changing them.
2. Infrequent or Nonexistent Updates
Unlike your phone or laptop that prompts for updates, many IoT devices don’t support over-the-air (OTA) updates or simply never get patched for vulnerabilities.
3. Low Computational Power
IoT devices are often lightweight and low-cost, which means limited RAM, CPU, or storage not enough for heavy-duty encryption or firewalls.
4. Always On, Always Online
IoT devices typically run 24/7 and are connected to networks non-stop, making them constantly available to attack surfaces.
5. Lack of Visibility
Most organizations and consumers have no idea how many IoT devices are connected to their networks let alone who has access to them.
Real-World IoT Security Incidents
IoT threats are no longer theoretical. They’re already happening:
The Mirai Botnet (2016)
A hacker used thousands of vulnerable IoT devices mostly webcams and routers to launch one of the biggest DDoS attacks in history, bringing down services like Netflix, Twitter, and Reddit.
Smart Baby Monitors Hacked
In multiple cases, hackers breached internet-connected baby monitors and spoke to children through the speakers. A horrifying example of how personal security can be compromised.
Jeep Cherokee Remote Hack
Security researchers remotely controlled a Jeep’s steering, brakes, and engine by exploiting vulnerabilities in the car’s infotainment system.
Casino Fish Tank Thermometer Hack
Attackers gained access to a Las Vegas casino’s network through a smart thermometer in a fish tank. From there, they stole high-roller data.
IoT Security in Businesses & Industries
While it’s easy to picture smart homes being attacked, the stakes are much higher in industries like manufacturing, healthcare, and logistics.
- In Healthcare: Compromised devices like pacemakers or infusion pumps can put lives at risk.
- In Manufacturing: IoT-enabled factories can experience production halts or sabotage through a single vulnerability.
- In Energy & Utilities: Smart grids and power stations, if hacked, could lead to nationwide blackouts or worse terrorist attacks.
IoT is becoming the nervous system of modern infrastructure, and an attack on one device could ripple across an entire ecosystem.
The Bigger Problem: Lack of Regulation
Unlike smartphones or laptops, IoT devices don’t yet fall under strict global cybersecurity regulations.
Some progress has been made:
- The U.S. IoT Cybersecurity Improvement Act (2020) sets minimum standards for federal agencies.
- The EU Cyber Resilience Act aims to enforce security throughout the product lifecycle.
But outside of these, consumer-grade and even commercial devices often go unchecked.
How Can We Secure IoT?
While we wait for better regulation and more responsible manufacturing, here’s what users, businesses, and developers can do today:
For Consumers:
- Change default credentials immediately.
- Regularly check for and apply firmware updates.
- Buy from reputable brands with clear security policies.
- Use network segmentation (e.g., separate your smart devices from your main Wi-Fi).
- Disable unused features or remote access options.
For Businesses:
- Implement Zero Trust architecture for IoT networks.
- Conduct IoT asset inventory and monitoring.
- Use intrusion detection and endpoint protection systems tailored for IoT.
- Train employees and IT staff about IoT risks.
- Partner with cybersecurity firms for regular penetration testing.
Developers & Manufacturers:
- Embed secure-by-design principles during product development.
- Avoid hardcoded credentials.
- Offer secure OTA update mechanisms.
- Encrypt data at rest and in transit.
- Participate in vulnerability disclosure programs.
The Future of IoT Security
As 5G and edge computing continue to grow, IoT will become even more deeply integrated into our lives and businesses.
What’s promising:
- More devices are now shipping with chip-level security modules.
- AI-powered security tools can help detect anomalies in real time.
- Regulations are slowly catching up.
But for now, we’re in a race a race between rapid innovation and responsible security. And the clock’s ticking.
Stay Smart About Smart Devices
IoT has the power to transform how we live and work. But with great connectivity comes great responsibility. Every smart device you add to your network is a potential door for cybercriminals to walk through.
So whether you’re a consumer buying smart plugs or a CTO deploying industrial sensors, security cannot be an afterthought anymore. It needs to be built in from day one.
Need Help Securing Your IoT Ecosystem?
At HashStudioz, we specialize in building, deploying, and securing custom IoT solutions for homes, startups, and enterprises. From secure firmware development to real-time threat monitoring, our experts can help you protect your connected future.
👉 Let’s talk about your IoT security strategy. Contact us today.

