In the realm of Industrial IoT (IIoT), GPS tracking systems play a pivotal role in ensuring operational transparency, asset monitoring, and logistics optimization. As industries adopt MQTT (Message Queuing Telemetry Transport) for transmitting location data due to its lightweight nature, a growing concern arises: security.
MQTT-based GPS trackers, while efficient, are highly vulnerable if not secured properly. Without the right protections, sensitive location data can be intercepted, manipulated, or used maliciously—posing a serious threat to enterprise operations and data privacy.
This blog will explore how to properly secure MQTT GPS trackers, examine common vulnerabilities, and provide actionable strategies for deploying secure, scalable GPS tracking solutions in industrial IoT ecosystems.
Understanding MQTT-Based GPS Trackers
MQTT is a publish/subscribe messaging protocol built for constrained environments, such as low-bandwidth, high-latency, or unreliable networks—making it ideal for GPS tracking in IIoT.
Key Components:
- GPS Tracker (Client): Publishes real-time location data (longitude, latitude, timestamp) to an MQTT broker.
- MQTT Broker: Acts as a message router between publishers and subscribers.
- Subscribers: Dashboards, cloud analytics systems, or mobile apps that process or visualize the data.
Why Use MQTT for GPS Tracking?
- Minimal bandwidth consumption
- Low power usage (ideal for battery-powered trackers)
- Simple implementation for embedded systems
- Asynchronous, real-time data delivery
While these benefits are compelling, they come at the cost of default protocol insecurity, which must be addressed before deployment in industrial settings.
Industrial IoT and the Importance of Security
In industrial applications—like oil and gas, logistics, smart agriculture, mining, and utilities—GPS data is tied to critical operations. If compromised, it can lead to:
1. Loss of Asset Location Control
This refers to the inability to track the real-time location of valuable industrial assets (vehicles, machinery, containers, etc.) due to compromised GPS data or system outages.
Impact: Operations lose visibility, resulting in misplaced equipment, delayed logistics, and disrupted workflows.
2. Theft or Hijacking of Equipment
If GPS data is intercepted or spoofed, attackers can physically steal or reroute equipment without detection, or impersonate legitimate trackers to conceal illicit activity.
Impact: Leads to financial losses, safety risks, and potential legal complications.
3. Business Disruptions
Compromised GPS systems can cause delays in delivery, stalled production lines, or loss of coordination in field operations. This breaks continuity in time-sensitive industries like logistics, mining, and agriculture.
Impact: Downtime, loss of revenue, and strained client relationships.
4. Regulatory Violations (e.g., GDPR, HIPAA, ISO/IEC 27001)
Industrial GPS data may fall under compliance mandates for data privacy and security. If location data is leaked, tampered with, or accessed unlawfully, organizations can be fined or penalized.
Impact: Legal action, audits, and substantial financial penalties.
5. Reputational Damage
News of a security breach—especially one involving stolen location data or equipment—can erode stakeholder trust, damage brand image, and reduce market competitiveness.
Impact: Loss of customer confidence, investor trust, and potential business opportunities.
MQTT Security Vulnerabilities in GPS Trackers
MQTT’s simplicity is also its greatest weakness. By default, MQTT:
- Transmits data in plaintext
- Has no encryption or authentication
- Lacks built-in access controls
- Offers limited message integrity checks
Common Threat Vectors:
- Man-in-the-middle (MitM) attacks: Attackers intercept location data between client and broker.
- Device spoofing: An attacker mimics a legitimate GPS tracker and sends fake coordinates.
- Topic hijacking: Malicious clients subscribe to topics they shouldn’t have access to.
- DoS attacks: Flooding the broker with invalid messages or overloading it with fake clients.
Key Security Measures for MQTT-Based GPS Trackers
To make MQTT-based GPS systems secure, implement the following multilayered defenses:
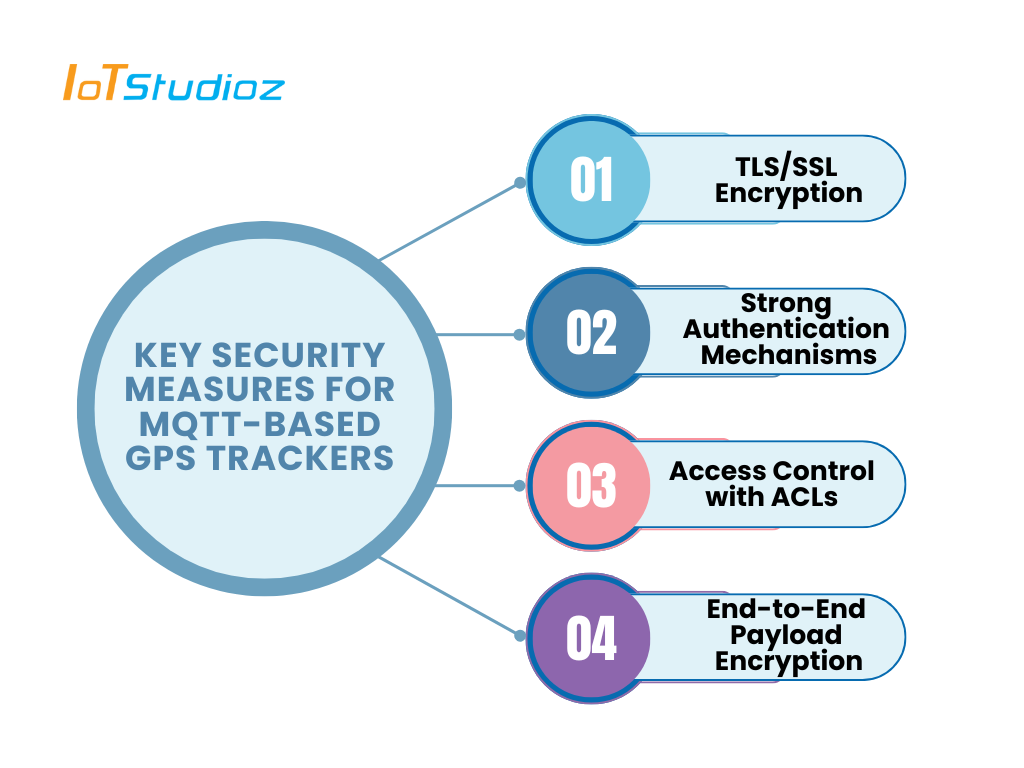
1. TLS/SSL Encryption
Transport Layer Security (TLS) is essential to encrypt MQTT traffic between clients and the broker.
- Use TLS 1.2 or higher
- Configure the broker to require TLS for all connections
- Use self-signed certificates or obtain from a CA (Certificate Authority) like Let’s Encrypt or DigiCert
- Disable plaintext ports (1883) and enforce secure ports (8883)
Result: Prevents data leakage and MitM attacks by encrypting data in transit.
2. Strong Authentication Mechanisms
Avoid basic username/password logins, especially hardcoded ones in firmware. Instead, implement:
- Username/Password with Rate Limiting
- X.509 Client Certificates: Ensures only authorized devices can connect.
- Token-based Authentication (e.g., JWT, OAuth2): Secure and scalable for enterprise systems.
- Two-Factor Authentication (2FA) for control panels and dashboards.
Result: Prevents unauthorized access to MQTT brokers and systems.
3. Access Control with ACLs (Access Control Lists)
MQTT brokers should implement topic-level access restrictions based on the client’s identity.
- Restrict each tracker to its own topic namespace.
- Disable wildcard subscriptions for unauthenticated users.
- Enforce “least privilege” policy.
Result: Prevents topic snooping, spoofing, and data leakage between clients.
4. End-to-End Payload Encryption
Even with TLS, encrypting data at the payload level adds another layer of protection.
- Encrypt GPS data using AES-256 or RSA public-key encryption before publishing.
- Only decrypt on the backend/cloud (never on intermediate relays).
- Securely manage encryption keys using HSMs or key vault services.
Result: Even if a TLS connection is compromised, payload data remains secure.
MQTT Security Best Practices
MQTT Security Best Practices refer to a set of recommended strategies and technical controls used to protect MQTT-based systems—like GPS trackers in Industrial IoT—from unauthorized access, data breaches, and operational threats.
1. Enforce TLS Across All Clients: Use TLS (Transport Layer Security) to encrypt all communications between MQTT clients (e.g., GPS trackers) and the broker.
Why: Prevents eavesdropping and man-in-the-middle (MitM) attacks by securing data in transit.
2. Disable Anonymous Access on Brokers: Require all MQTT clients to authenticate using credentials or certificates.
Why: Stops unauthorized devices from connecting and publishing or subscribing to topics.
3. Rotate Client Credentials/Certificates Regularly: Implement automatic expiration and renewal of credentials or client certificates.
Why: Limits exposure in case of credential theft and supports better lifecycle management.
4. Monitor for Unusual Connection Patterns (Rate, Volume): Track metrics such as connection frequency, message size, and topic activity to detect anomalies.
Why: Helps identify potential attacks (e.g., DDoS, brute-force logins, or rogue devices).
5. Use MQTT v5.0: Adopt MQTT version 5.0, which introduces advanced features like:
- Enhanced error reporting with reason codes
- User properties for message-level metadata
- Session expiry, topic aliasing, and flow control
Why: Improves reliability, debugging, and fine-grained control over client behavior.
6. Harden Broker OS with Firewalls, SELinux, or AppArmor: Secure the operating system running the MQTT broker with:
- Firewalls to restrict open ports
- SELinux or AppArmor for mandatory access controls
Why: Adds an extra layer of security at the OS level, reducing the attack surface.
Real-World Security Breaches
- Fleet Tracking Leak (2019): Thousands of GPS trackers were found with default credentials and no TLS, exposing location data across the globe.
- MQTT Open Brokers (2020): Security researchers found over 35,000 MQTT brokers exposed to the internet with no authentication.
- Smart Agriculture Attack (2021): Attackers intercepted MQTT packets to track farming equipment and disrupt harvest operations.
Tools and Libraries to Implement Security
Here are recommended tools and services for securing MQTT-based GPS trackers:
| Tool | Purpose |
| Mosquitto | Lightweight MQTT broker with TLS and ACL support |
| HiveMQ | Enterprise MQTT broker with plugins and advanced security |
| Certbot | Automates TLS certificate generation |
| OpenSSL | Tool for managing keys, certificates, and testing TLS |
| MQTT.fx / MQTT Explorer | GUI for secure MQTT message testing |
| AWS IoT Core / Azure IoT Hub | Secure cloud MQTT broker alternatives with IAM and token support |
Conclusion
As the backbone of real-time tracking in IIoT networks, MQTT-based GPS trackers must be protected with robust, multilayered security measures. From encrypted transport and authenticated access to secure payloads and access control policies, each layer adds essential protection.
Ignoring MQTT security doesn’t just risk data breaches—it can disrupt entire supply chains and industrial operations.
FAQs
Q1: Is MQTT secure enough for industrial applications?
Not by default. MQTT is insecure unless combined with TLS, authentication, and ACLs. With proper configurations, it becomes secure enough for IIoT use.
Q2: Do I need both TLS and payload encryption?
Yes. TLS protects data in transit, while payload encryption protects the message itself—even if TLS is broken.
Q3: What’s the best MQTT broker for secure deployments?
For enterprise-grade deployments, HiveMQ and EMQX offer advanced security. Mosquitto is good for small-scale and highly customizable use cases.
Q4: Can MQTT be used over mobile networks?
Absolutely. MQTT is designed for unreliable networks and performs well over 2G/3G/4G with low data overhead.
Q5: How often should certificates or tokens be rotated?
Ideally, rotate them every 90 days. For sensitive or mission-critical applications, consider shorter durations (e.g., 30–60 days) and implement automated renewal processes.