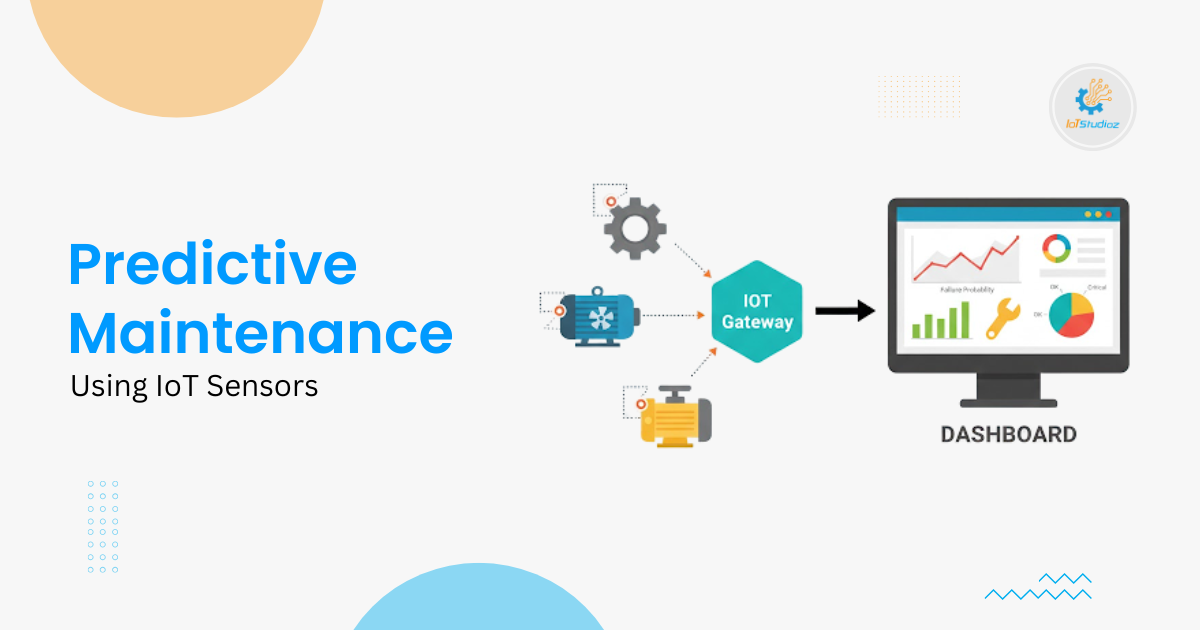
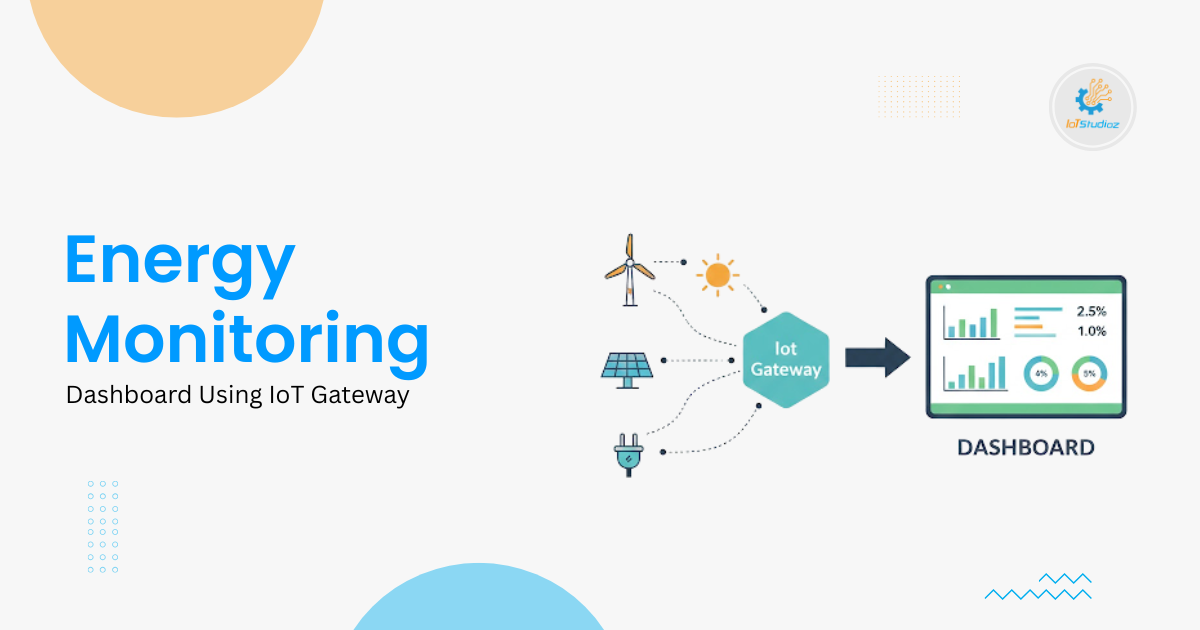
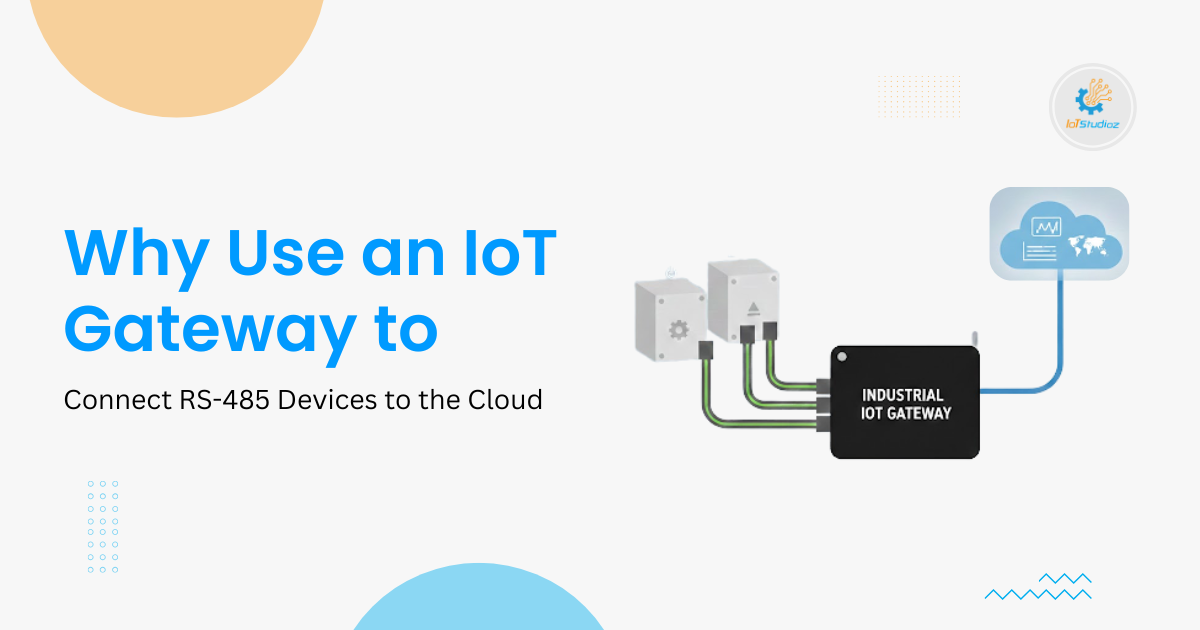
Remote Asset Monitoring for Distributed Sites
In modern industrial and commercial settings, monitoring assets across multiple locations has become essential. Remote asset monitoring goes beyond simple location tracking. It involves real-time condition checking, predictive alerts, and